Have you considered the network security of your IoT devices? Poor security measures can make your device vulnerable to attacks, allowing someone to take over your device or rack up huge data bills by using your SIM card in other applications.
In the past, we've written about major security incidents in IoT and how to avoid vulnerabilities in your deployments. This time, we'll focus on 7 steps you should take to protect your devices and SIM cards against misuse from the network and management layer perspective.
Before we move on, you should always (stress)test, analyze, and configure your IoT devices according to their specifications and use cases to ensure they work properly and securely and can be configured and debugged remotely in case of issues.
1. When possible, use the MFF2 embedded SIM form factor. This provides extra security against possible SIM theft as it is nearly impossible to desolder from the device's PCB.
2. Create a private APN. A private Access Point Name enables authentication to the network with defined rules and differentiates the traffic from a device's and application's perspective:
- Allow traffic to only predefined IP addresses
- IP allocation (define dynamic or Static IP Pools)
Customize APN naming
3. Create an IPsec VPN, a Virtual Private Network with a Private APN, where data is not passed through the public internet and is isolated in the VPN tunnel.
- VPN enables the use of dynamic IP pools and static private IP pools within the VPN for remote access and increased security.
- VPNs serve the purpose of security and data privacy as the data is not moving over the public internet.
4. Deactivate communication that you don't use on your device. This could be as simple as disabling voice and SMS capabilities, but it will ensure that malicious people can't access your device using those functions.
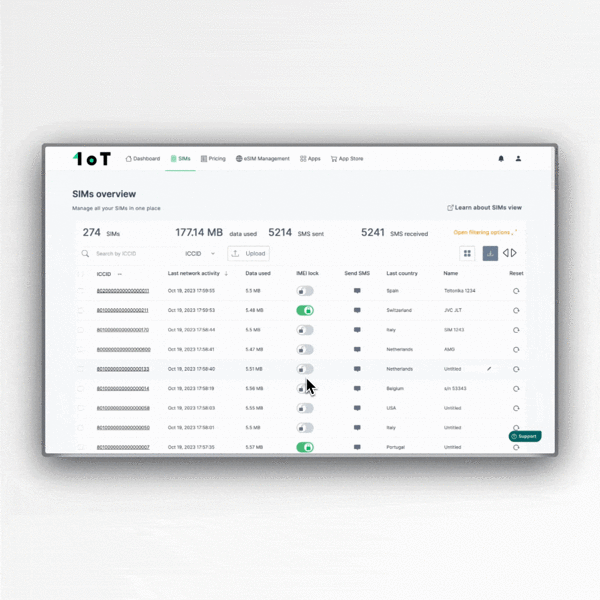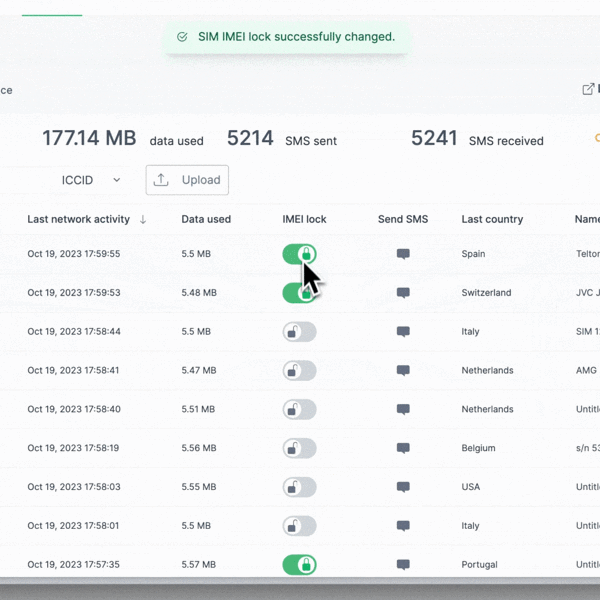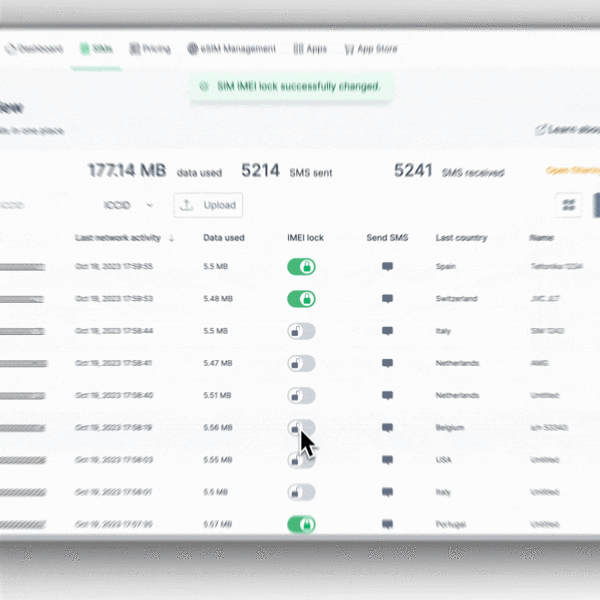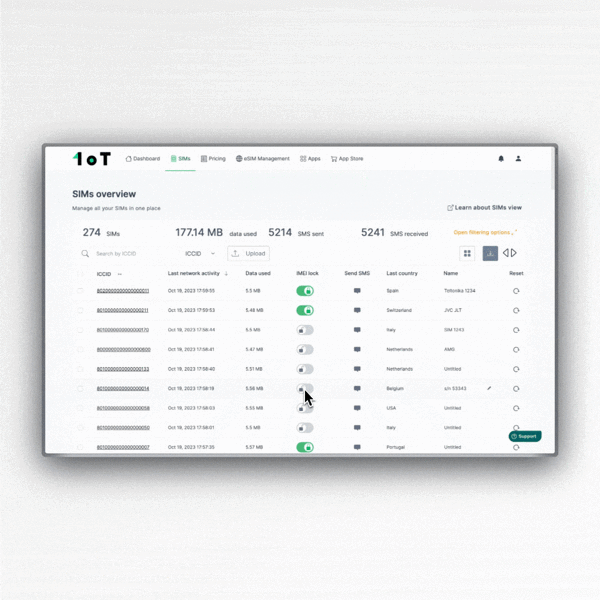
5. Activate the IMEI Lock
The IMEI lock is a security feature that ties the SIM to a specific device via its IMEI number. When the network identifies a new device's IMEI, the connectivity management platform (CMP) will automatically switch the SIM offline, and unwanted people won't be able to misuse it by plugging it into another device.
The feature is available in the 1oT Terminal App Store as a separate subscription. The IMEI lock feature depends on natural delays due to telecommunications routing between the device and central servers that control the mechanism and is not immediate.
6. Set SMS and data limits
CMPs, like 1oT Terminal, let you set up data and SMS limits to prevent unexpected data costs due to device malfunction or misuse. Once the device reaches its monthly limit, all services will be terminated, and the SIM will go to the offline status. However, the feature depends on natural telecommunications routing delays, carrier-specific integrations, and technical capabilities, which is why the actions are not immediate.
7. Automate workflows and set up notifications
The Workflow automation app allows you to set up various actions and notifications based on consumption, location, and date-based triggers. It is available in the 1oT Terminal App Store as a separate subscription. The feature depends on natural telecommunications routing delays, carrier-specific integrations, and technical capabilities. Therefore, the actions triggered are not immediate.
For more information on IoT device security, you can check out GSMA's IoT Device Connection Efficiency Guidelines and 1oT's FAQ. If you want to talk more about making your devices secure during your R&D phase, reach out to sales@1ot.com!